最适合您的 Action 的账号关联类型应该既能为用户提供最便捷的体验,又能满足您的应用或业务的需求。选择关联类型主要取决于以下因素:
- 是否允许通过语音创建账号
- 您是否希望用户能够使用非 Google 帐号登录您的服务
- 您的服务是否可以存储机密信息(即客户端密钥)
要确定理想的帐号关联类型,请按以下步骤操作:
- 考虑确定您的首选登录类型部分中的问题。
- 请参阅决策树,选择关联类型。
- 转到与您选择的初始类型对应的部分,进一步优化其工作原理。
确定您的首选登录类型
在查阅决策树之前,请考虑以下问题:
- 您是否希望所有用户都拥有 Google 账号?
- 如果您的 Action 仅以 Google 助理为目标平台,那么您的所有用户都应该有 Google 帐号。如果您的 Action 以 Google 助理以外的平台为目标平台,那么所有用户都不能拥有 Google 帐号。
- 如果您的服务已有现有用户,则其中一些用户可能没有 Google 帐号,或者没有使用 Google 帐号登录您的服务。
- 如果您有 OAuth 实现,是否可以扩展它以支持 Google 协议?
- 为了支持 Google 协议,您需要能够向令牌交换端点添加
intent=get和intent=create功能。此功能允许 Google 检查您的后端中是否已存在用户,并分别请求在您的服务上创建新帐号。
- 为了支持 Google 协议,您需要能够向令牌交换端点添加
请按照以下决策树,确定最适合您和您的用户的帐号关联类型:
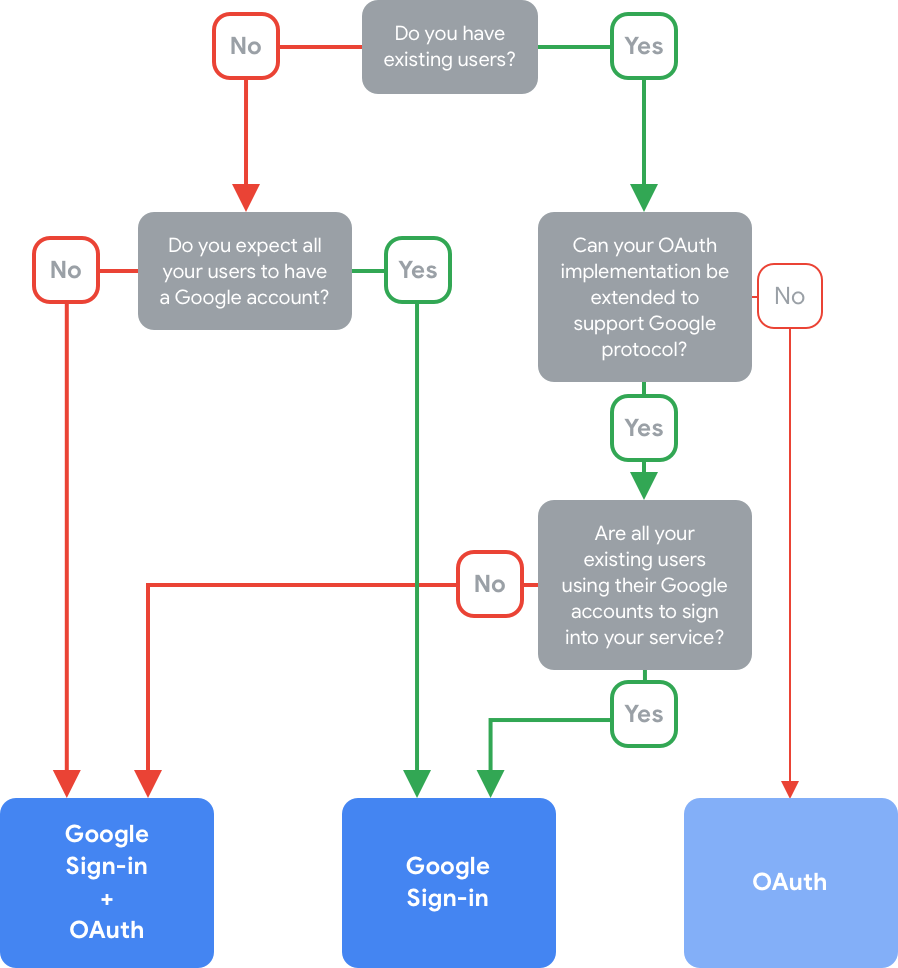
选择关联类型后,请继续阅读下文的相应部分,详细了解其运作方式,并进一步决定账号关联在 Action 中的运作方式。
OAuth 和 Google 登录
OAuth 和 Google 登录 (GSI) 关联类型会在基于 OAuth 的帐号关联基础上添加 GSI,这样既能享受 GSI 的优势(例如,面向 Google 用户提供基于语音的关联),还能为使用非 Google 帐号注册服务的用户启用帐号关联。这种关联类型对最终用户特别有益,因为它为 Google 用户提供顺畅的流程,并可供非 Google 用户使用。如需详细了解 OAuth 和 GSI 关联类型的工作原理,请参阅 OAuth 和 Google 登录概念指南。
优化 OAuth 和 Google 登录关联类型
在 Action 中使用 OAuth 和 GSI 账号关联类型时,您需要在 Actions 控制台中指定以下问题的答案,以定义其运作方式:
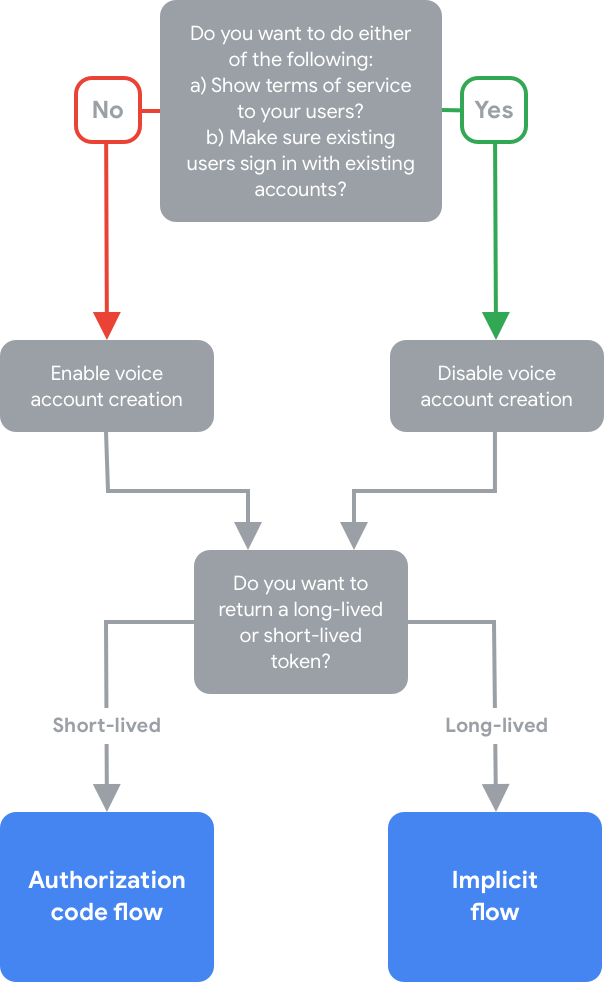
您是想允许在您的网站上创建语音帐号,还是仅允许创建帐号?
通常,您应允许通过语音创建帐号,以便使用未经过筛查的设备的用户无需转移到其他设备即可创建帐号。如果您不允许通过语音创建帐号,Google 助理会打开您为用户身份验证提供的网站网址,并将用户定向到手机以继续完成帐号关联流程。
但是,如果出现以下任一情况,您不应允许通过语音创建帐号:
- 您需要完全控制帐号创建流程。例如,您可能需要在创建帐号时向用户显示服务条款或接收其他类型的通知。
- 您希望确保已拥有您账号的用户使用该账号登录。例如,如果您提供会员回馈活动,并且不希望用户失去其帐号中累积的积分,您可能希望用户继续使用其现有帐号。
您想使用授权代码流程还是隐式流程?
授权代码流程和隐式流程的不同之处在于授权代码流程需要第二个端点,即令牌交换端点。此端点使用刷新令牌来生成新的短期访问令牌,而不会提示用户再次登录。
相反,如果您使用隐式流程,则会向 Google 返回一个长期有效的访问令牌,该令牌通常不需要重新生成。如需详细了解授权代码和隐式流程,请参阅 OAuth 和 Google 登录概念指南。
Google 建议您在 Action 中使用授权代码流程,因为它更安全。但是,如果您的服务无法存储机密信息(即客户端密钥),请改用隐式流程。例如,您必须对单页应用 (SPA) 等公共客户端使用隐式流程。
在考虑了这些决策点后,请查阅以下决策树:
Google 登录功能
指定 GSI 关联类型后,您的 Action 可以在对话期间请求访问用户的 Google 个人资料,并使用个人资料信息来检查用户是否位于服务后端。如果用户不存在,他们可以使用其 Google 个人资料信息在您的系统中创建新帐号。
对于 GSI,您必须启用通过语音创建帐号的功能,以便用户通过语音完成整个流程。如需详细了解 GSI,请参阅 Google 登录概念指南。
OAuth
如果选择 OAuth 关联类型,用户将通过标准 OAuth 2 流程登录。 OAuth 关联类型支持两种业界标准 OAuth 2.0 流程:隐式和授权代码流程。
Google 不建议单独使用 OAuth 关联类型,因为如果用户使用的是未经筛查的设备,该关联类型需要将用户从语音转移到屏幕来完成登录流程。如果您已有 OAuth 2 服务器实现,并且无法扩展令牌交换端点以添加对 Google 协议的支持,从而自动关联以及基于 ID 令牌创建帐号,则可以考虑使用此流程。如需了解详情,请参阅 OAuth 概念指南。
优化流程
在 Action 中使用 OAuth 账号关联类型时,您必须在 Actions 控制台中指定以下问题的回答来定义其运作方式:
您想使用授权代码流程还是隐式流程?
OAuth 关联类型支持两种业界标准 OAuth 2.0 流程:隐式和授权代码流程。授权代码流程和隐式流程的不同之处在于授权代码流程需要第二个端点,即令牌交换端点。此端点使用刷新令牌生成新的短期访问令牌,而不会提示用户再次登录。
相反,如果您使用隐式流程,则会向 Google 返回一个长期有效的访问令牌,该令牌通常不需要重新生成。如需详细了解授权代码和隐式流程,请参阅 OAuth 概念指南。
Google 建议您在 Action 中使用授权代码流程,因为它更安全。但是,如果您的服务无法存储机密信息(即客户端密钥),请改用隐式流程。例如,您必须对单页应用 (SPA) 等公共客户端使用隐式流程。
