将通行密钥集成到您的应用或网站中,仅仅是个开始 通行密钥的历程完成初始部署后,您要应对的其中一个挑战 确保用户了解什么是通行密钥 创建它们。
建议您在用户使用 Google 账号登录后立即创建通行密钥 以及使用第二重身份验证。记住密码和 以及在不同应用和工具之间切换时输入动态密码 会让用户感到失望建议现在创建通行密钥 合适的时机,因为用户很可能会感到这种沮丧。
除了自我管理的促销活动外,Google 密码管理工具现在还可以 建议您代表您的网站或应用创建新的通行密钥。
用户体验
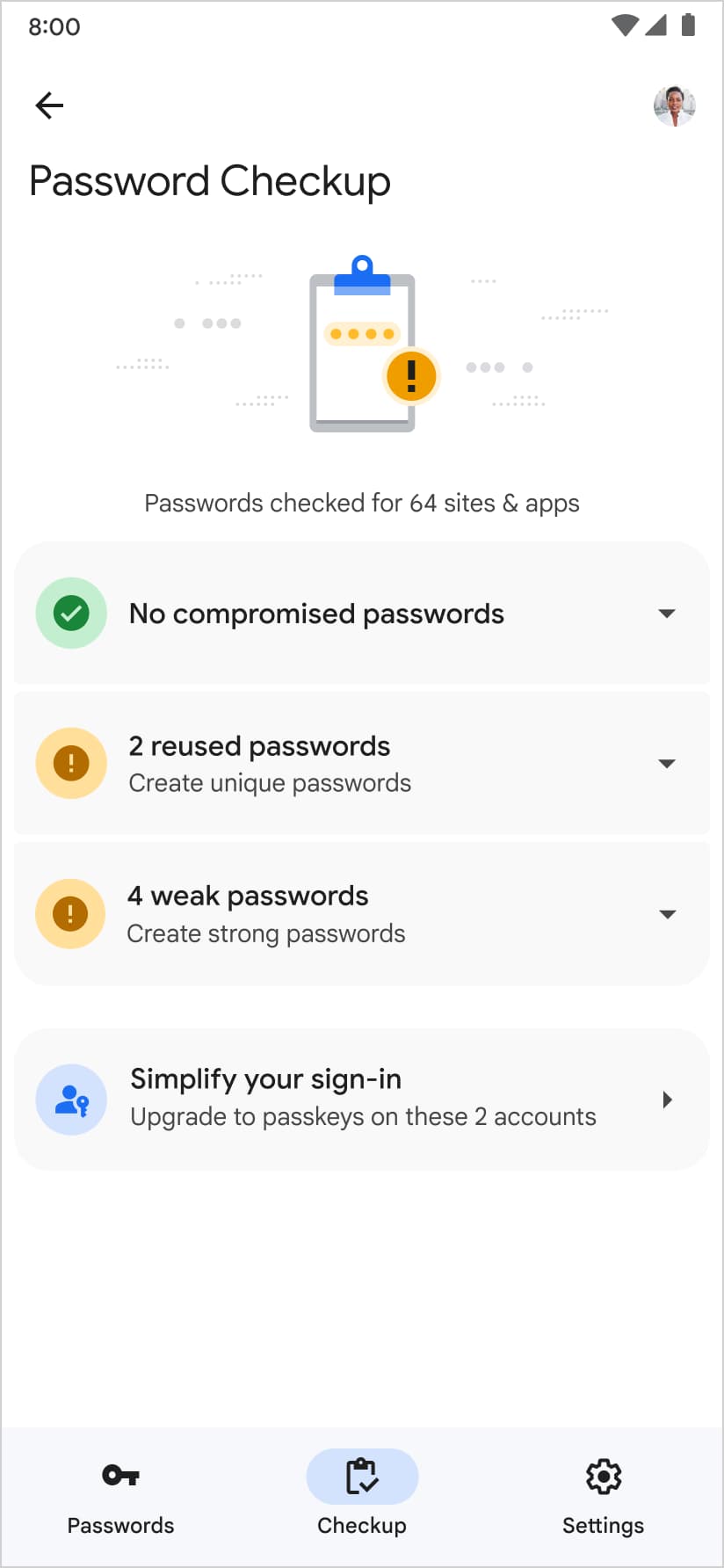
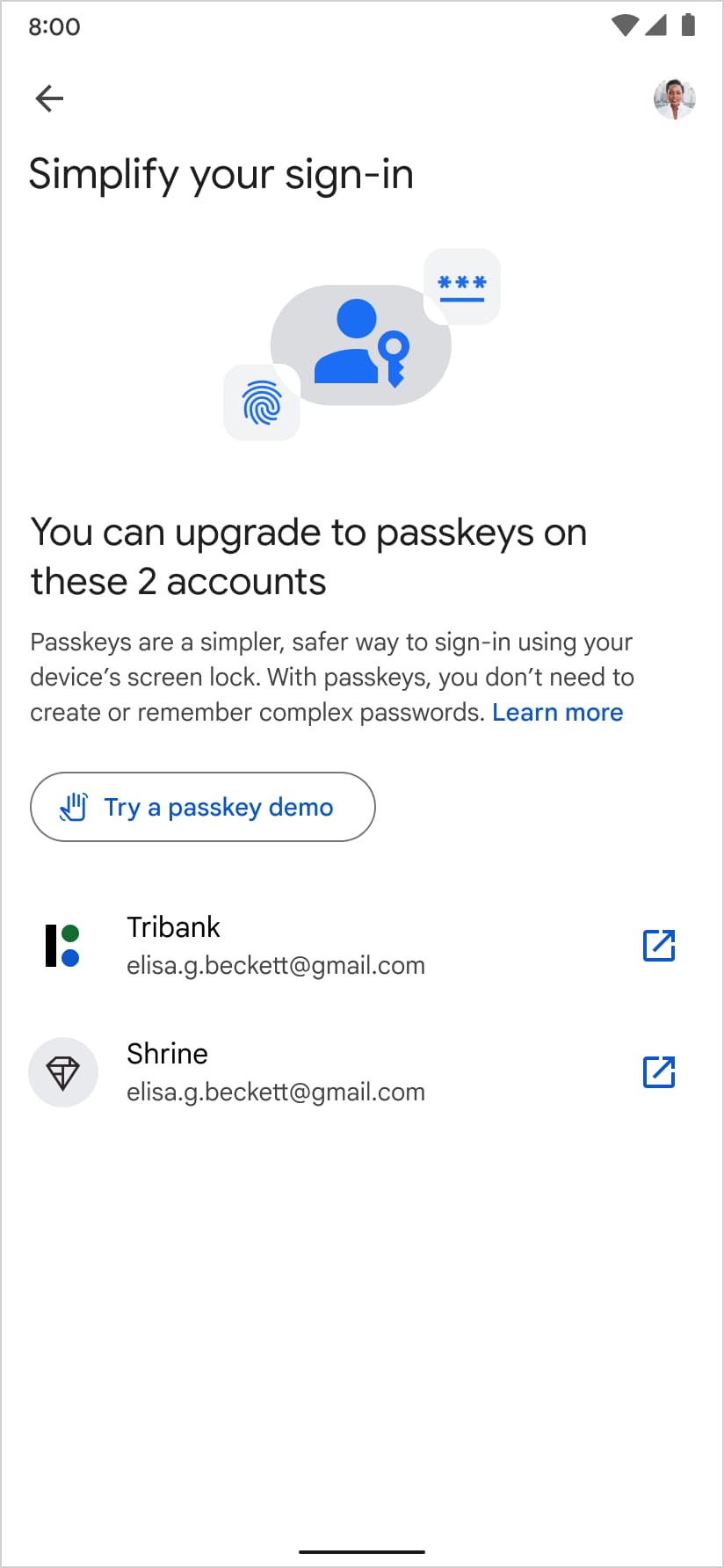
在 Pixel 设备上,Google 密码管理工具发现您的网站或应用 支持通行密钥、建议用户创建新的通行密钥,并引导他们 通行密钥创建页面
<ph type="x-smartling-placeholder">
添加通行密钥端点
若要在 Google 密码管理工具中启用通行密钥升级功能,请将 JSON 文件添加到您的
服务器位于 /.well-known/passkey-endpoints。这称为“通行密钥端点”
知名网址”它是一个开放的
协议
让相关各方正式公布对通行密钥的支持,并提供
用于注册和管理通行密钥的直接链接。采用
对其他平台的影响。
例如,如果信赖方的网域是
https://passkeys-demo.appspot.com,则网址为
https://passkeys-demo.appspot.com/.well-known/passkey-endpoints。
从端点提供如下所示的 JSON 文件:
{
"enroll": "https://passkeys-demo.appspot.com/home",
"manage": "https://passkeys-demo.appspot.com/home"
}
enroll 应指向用户可以创建通行密钥的网址。manage
应指向可供用户管理已创建通行密钥的网址。
在以下情况下,Google 密码管理工具会引用您的通行密钥端点知名网址: 有密码输入,但 Google 密码中没有通行密钥条目 管理者。
确定用于部署通行密钥端点知名网址的主机
当通行密钥注册网址位于 id.example.com 但
通行密钥位于 example.com,通行密钥端点应托管在哪个网址?
通行密钥端点应托管在 RP ID 网域中。在上面的示例中,
端点网址应为 https://example.com/.well-known/passkey-endpoints。
即使您的密码输入项出现在您设备上的https://id.example.com中,
那么这无关紧要
填写通行密钥升级表单
部署通行密钥端点知名网址后,请填写此表单。
支持 Android 应用
如需引导用户前往 Android 应用的通行密钥创建页面,您可以 Android App Links,以便 系统会将您拥有的网址重定向到您应用的特定 fragment。