与服务账号工作流程类似,单用户身份验证流程利用 Google Ads 界面提供的授权和用户管理功能,向应用授予对所有必需账号的访问权限。此身份验证工作流包含两个步骤:
- 您向单个用户授予对应用应管理的所有 Google Ads 账号的访问权限。
- 用户授权您的应用代表其管理 Google Ads 账号,从而授予该应用对所有 Google Ads 账号的访问权限。
由于只涉及一个用户,因此您可以依赖 gcloud CLI 或 GenerateUserCredential 代码示例等工具,而不是构建自己的 OAuth 2.0 用户身份验证流程。
此工作流的相关使用情形是,当您的账号可以通过少数几个用户登录信息(例如 3-4 个用户)进行访问时,与使用命令行工具(例如 gcloud CLI)获取 3-4 个用户的授权相比,构建完整的 OAuth 用户身份验证工作流的开发工作量并不合理。
缺点
与服务账号工作流相比,此流程存在以下缺点:
- 用户身份验证工作流要求您在 Google Cloud 控制台中创建 OAuth 2.0 客户端 ID 和密钥,这比创建服务账号和密钥需要更多配置步骤。
- 您的应用可能需要接受额外的 Google Cloud 应用验证流程。
- 如果已获授权的用户离开团队或公司,那么如果您从自己的账号中移除该用户或停用该用户账号,您的应用可能会停止运行。服务账号不与个别用户相关联,因此可以避免此风险。
- 授权 Google Ads 账号的用户应采取额外的预防措施,例如启用双重身份验证,以防范其 Google 账号因安全性差、遭受恶意软件攻击或遭受钓鱼式攻击而遭到入侵。服务账号不太容易受到此问题的影响,因为其中一些攻击模式并不直接适用于服务账号。
生成凭据
按照说明为您的应用配置 OAuth 权限请求页面,并添加
https://www.googleapis.com/auth/adwords作为 OAuth 2.0 范围。如需了解详情,请参阅设置 OAuth 权限请求页面。按照说明创建客户端 ID 和客户端密钥。创建 OAuth 2.0 客户端后,请先点击其“下载 OAuth 客户端”图标,然后在后续屏幕上点击“下载 JSON”按钮,下载该客户端的 JSON 文件。将文件另存为
credentials.json。确定一个有权访问您想使用应用管理的所有 Google Ads 账号的用户账号。如果某些账号缺少访问权限,请按照说明授予必要的访问权限。
下载并安装 gcloud CLI。安装完成后,通过在命令行提示符下运行
gcloud version命令,验证该工具是否正常运行。输出可能如下所示。:~$ gcloud version Google Cloud SDK 492.0.0 alpha 2024.09.06 beta 2024.09.06 bq 2.1.8 bundled-python3-unix 3.11.9 core 2024.09.06 enterprise-certificate-proxy 0.3.2 gcloud-crc32c 1.0.0 gsutil 5.30运行 gcloud CLI 工具,生成 OAuth 2.0 刷新令牌:
gcloud auth application-default
login --scopes=https://www.googleapis.com/auth/adwords,https://www.googleapis.com/auth/cloud-platform
--client-id-file=<path_to_credentials.json>credentials.json文件来自上一步。gcloud命令会在新的浏览器窗口中打开 Google 账号登录窗口,并引导您完成 OAuth 2.0 身份验证步骤。请务必以您在上一步中选择的用户身份登录。如果您的应用未经验证,您可能会看到警告界面。在这种情况下,您可以放心地点击显示高级链接,然后点击前往 PROJECT_NAME(未验证)选项。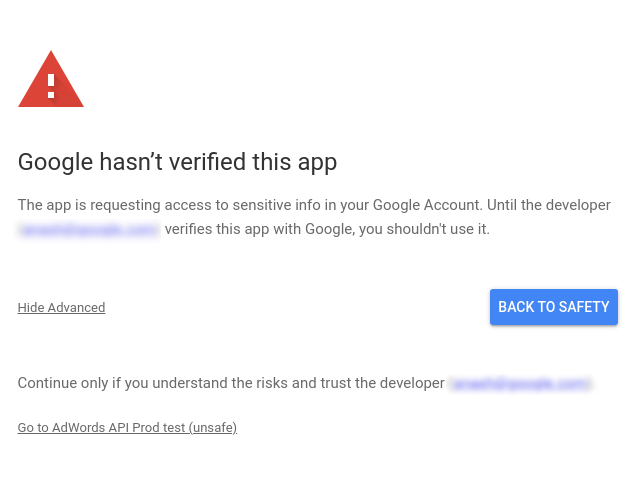
验证范围后,点击继续按钮以授予权限。浏览器会导航到
https://cloud.google.com/sdk/auth_success,表明身份验证成功。该页面会显示以下消息:Authorization code granted. Close this tab.gcloud命令会输出以下消息:Credentials saved to file: [/****/.config/gcloud/application_default_credentials.json]现在,打开
application_default_credentials.json文件。其内容应类似于以下内容:{ "account": "", "client_id": "******.apps.googleusercontent.com", "client_secret": "******", "refresh_token": "******", "type": "authorized_user", "universe_domain": "googleapis.com" }
客户端库配置
选择与您的编程语言对应的标签页,查看有关如何配置客户端库的说明。
Java
在 ads.properties 文件中配置以下键。
api.googleads.clientId=INSERT_CLIENT_ID_HERE
api.googleads.clientSecret=INSERT_CLIENT_SECRET_HERE
api.googleads.refreshToken=INSERT_REFRESH_TOKEN_HERE
api.googleads.loginCustomerId=INSERT_LOGIN_CUSTOMER_ID_HERE
如需了解其他选项,请参阅配置指南。
.NET
您可以在运行时初始化 GoogleAdsClient 实例,使用从您要对其账号进行 API 调用的用户处获得的凭据。
GoogleAdsConfig config = new GoogleAdsConfig()
{
OAuth2Mode = OAuth2Flow.APPLICATION,
OAuth2ClientId = "INSERT_OAUTH2_CLIENT_ID",
OAuth2ClientSecret = "INSERT_OAUTH2_CLIENT_SECRET",
OAuth2RefreshToken = "INSERT_OAUTH2_REFRESH_TOKEN",
...
};
GoogleAdsClient client = new GoogleAdsClient(config);
如需了解其他选项,请参阅配置指南。
Python
在 google-ads.yaml 文件中配置以下键。
client_id: INSERT_OAUTH2_CLIENT_ID_HERE
client_secret: INSERT_OAUTH2_CLIENT_SECRET_HERE
refresh_token: INSERT_REFRESH_TOKEN_HERE
login_customer_id: INSERT_LOGIN_CUSTOMER_ID_HERE
如需了解其他选项,请参阅配置指南。
PHP
在 google_ads_php.ini 中配置以下键。
[GOOGLE_ADS]
loginCustomerId = "INSERT_LOGIN_CUSTOMER_ID_HERE"
[OAUTH2]
clientId = "INSERT_OAUTH2_CLIENT_ID_HERE"
clientSecret = "INSERT_OAUTH2_CLIENT_SECRET_HERE"
refreshToken = "INSERT_OAUTH2_REFRESH_TOKEN_HERE"
如需了解其他选项,请参阅配置指南。
Ruby
在 google_ads_config.rb 文件中配置以下键。
Google::Ads::GoogleAds::Config.new do |c| c.client_id = 'INSERT_CLIENT_ID_HERE' c.client_secret = 'INSERT_CLIENT_SECRET_HERE' c.refresh_token = 'INSERT_REFRESH_TOKEN_HERE' c.developer_token = 'INSERT_DEVELOPER_TOKEN_HERE' c.login_customer_id = 'INSERT_LOGIN_CUSTOMER_ID_HERE' end
如需了解其他选项,请参阅配置指南。
Perl
在 googleads.properties 文件中配置以下键。
clientId=INSERT_OAUTH2_CLIENT_ID_HERE clientSecret=INSERT_OAUTH2_CLIENT_SECRET_HERE refreshToken=INSERT_OAUTH2_REFRESH_TOKEN_HERE loginCustomerId=INSERT_LOGIN_CUSTOMER_ID_HERE
如需了解其他选项,请参阅配置指南。
curl
首先,使用 HTTP 客户端获取 OAuth 2.0 访问令牌。本指南使用 curl 命令。
curl \
--data "grant_type=refresh_token" \
--data "client_id=CLIENT_ID" \
--data "client_secret=CLIENT_SECRET" \
--data "refresh_token=REFRESH_TOKEN" \
https://www.googleapis.com/oauth2/v3/token现在,您可以在 API 调用中使用访问令牌了。以下示例展示了如何使用 GoogleAdsService.SearchStream 方法运行广告系列报告,以检索您账号中的广告系列。本指南不涉及报告的详细信息。
curl -i -X POST https://googleads.googleapis.com/v23/customers/CUSTOMER_ID/googleAds:searchStream \
-H "Content-Type: application/json" \
-H "Authorization: Bearer ACCESS_TOKEN" \
-H "developer-token: DEVELOPER_TOKEN" \
-H "login-customer-id: LOGIN_CUSTOMER_ID" \
--data-binary "@query.json"query.json 的内容如下所示:
{
"query": "SELECT campaign.id, campaign.name, campaign.network_settings.target_content_network FROM campaign ORDER BY campaign.id"
}
